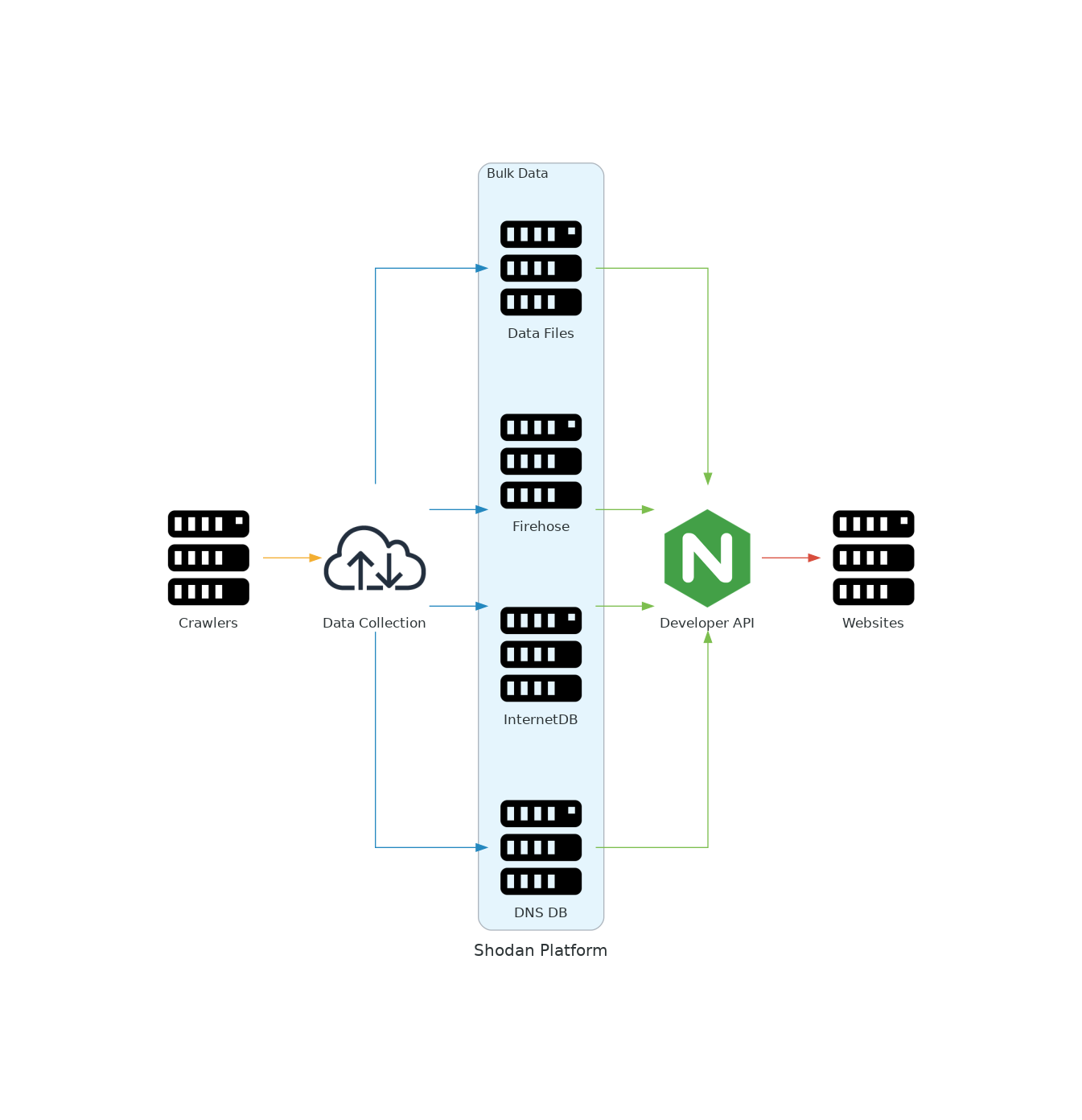
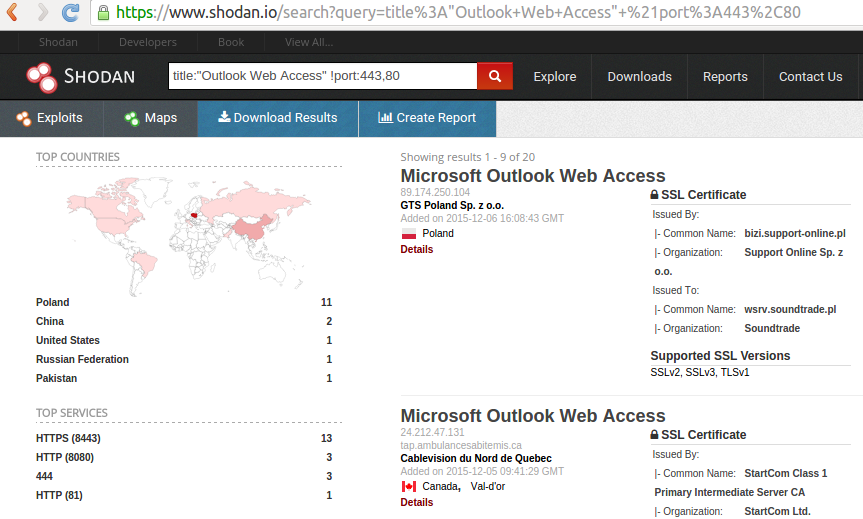
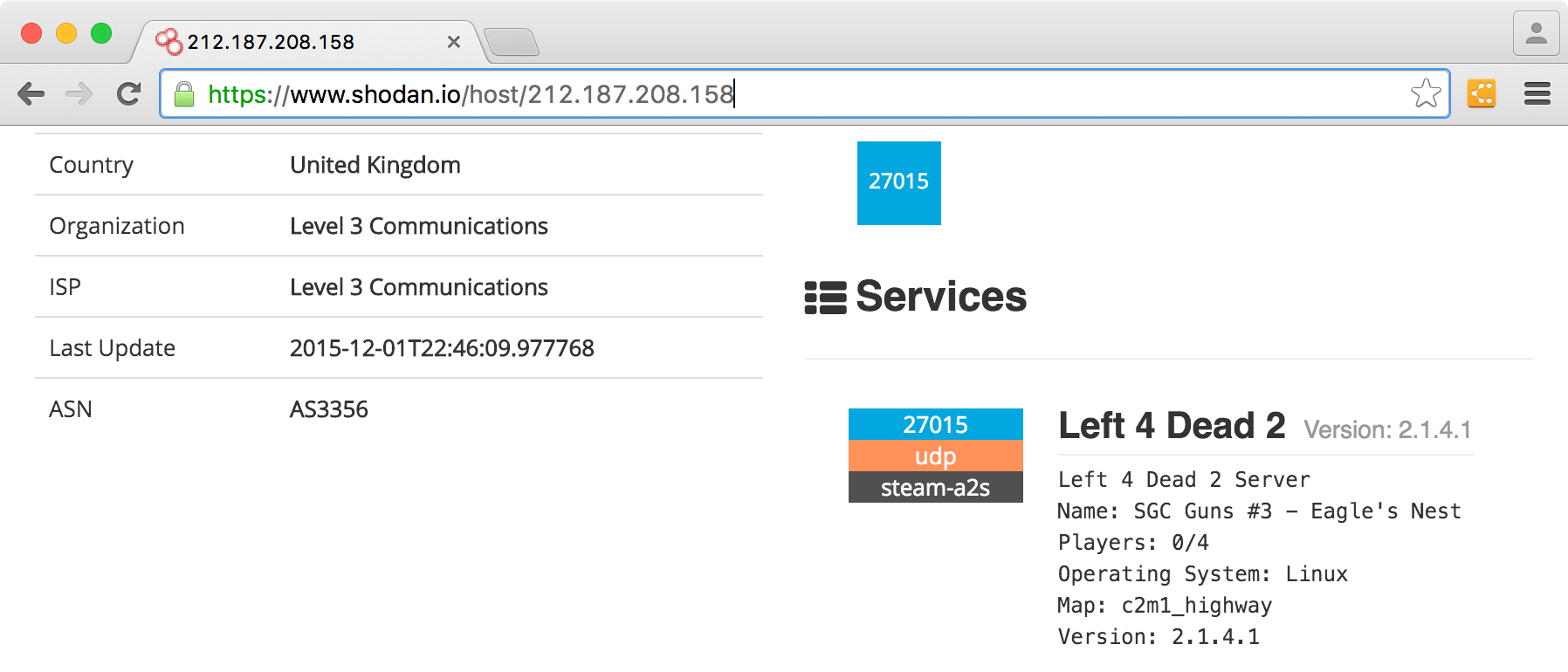
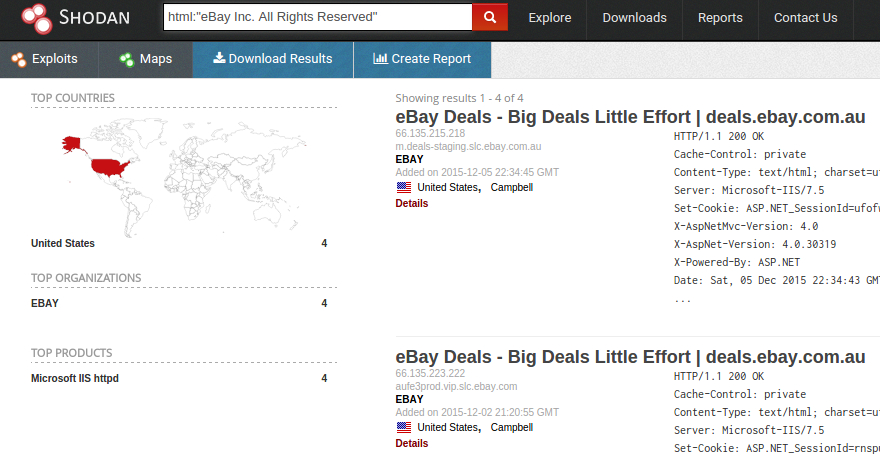
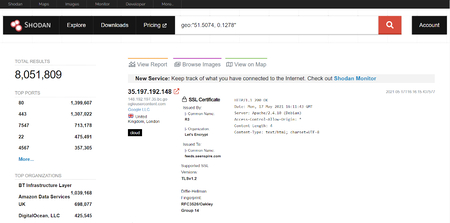
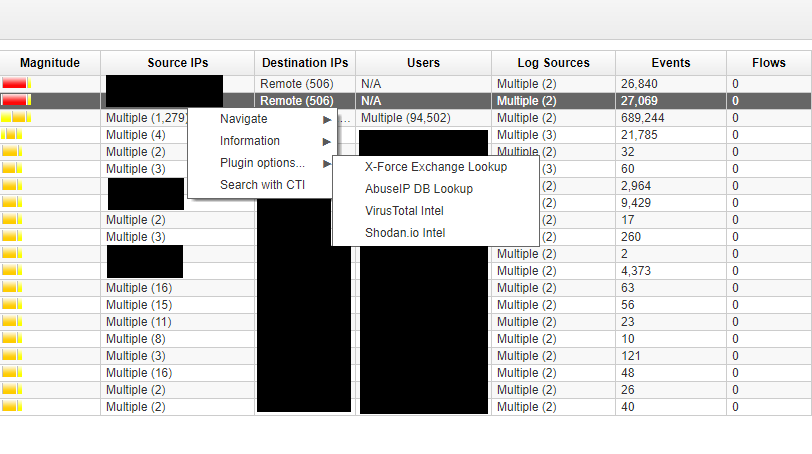
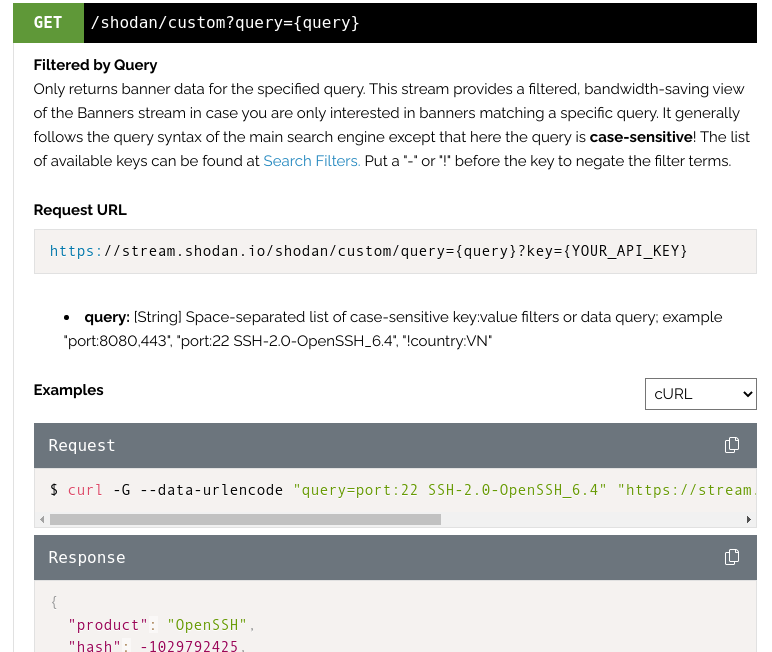
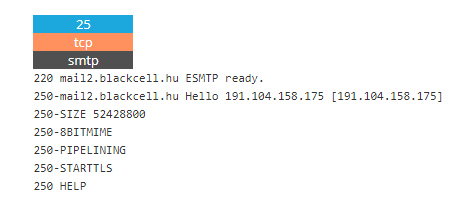
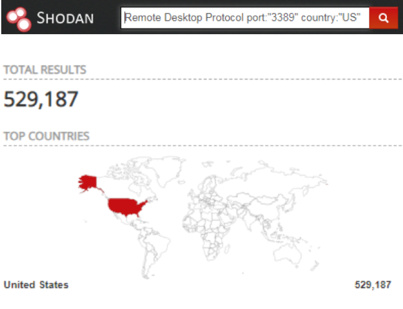
Shodan on Twitter: "@ric_rosasr Shodan actually tests for the Eternalblue vulnerability whereas your search query just lists SMB services that meet the potential criteria. You can count the number of services vulnerable
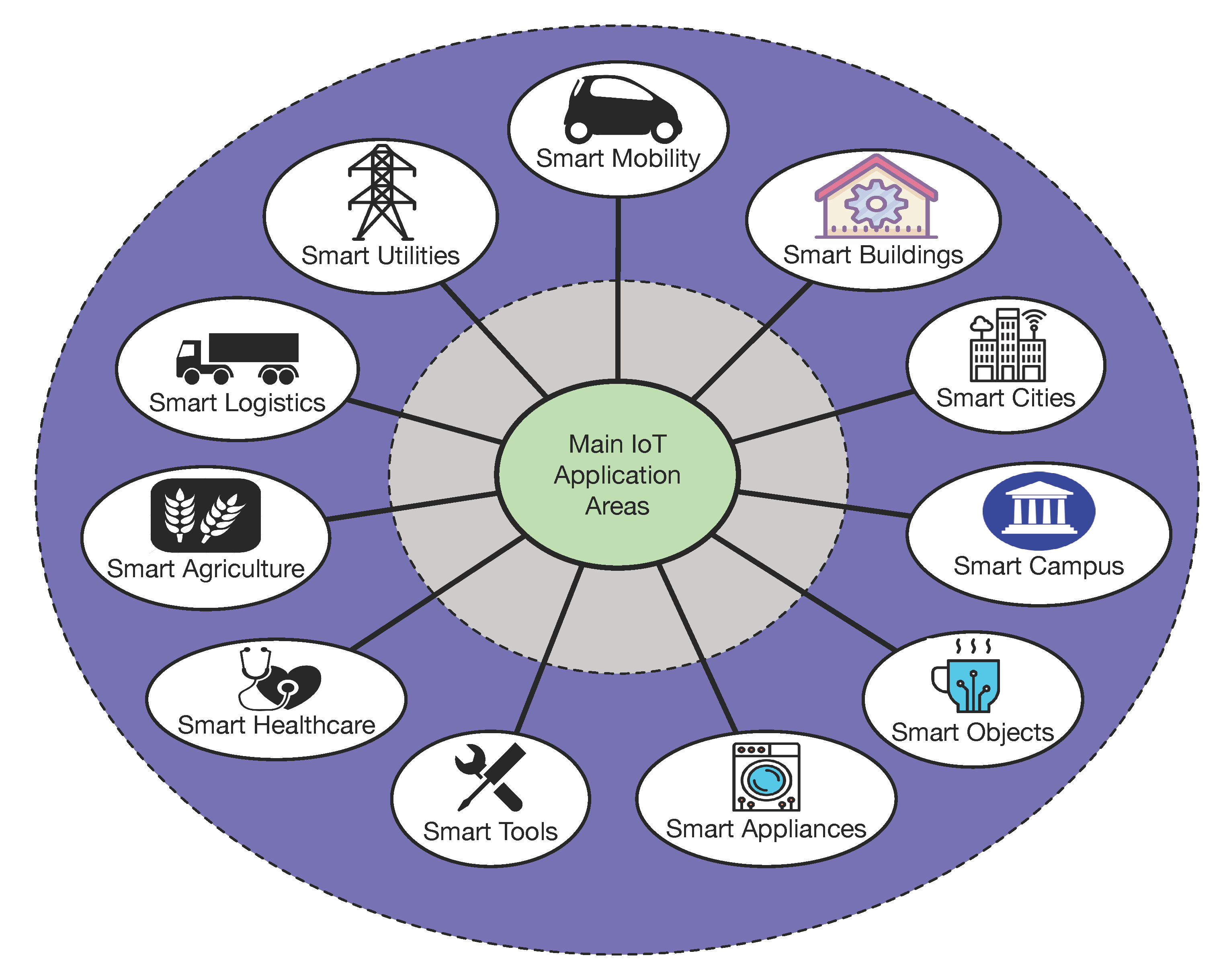
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
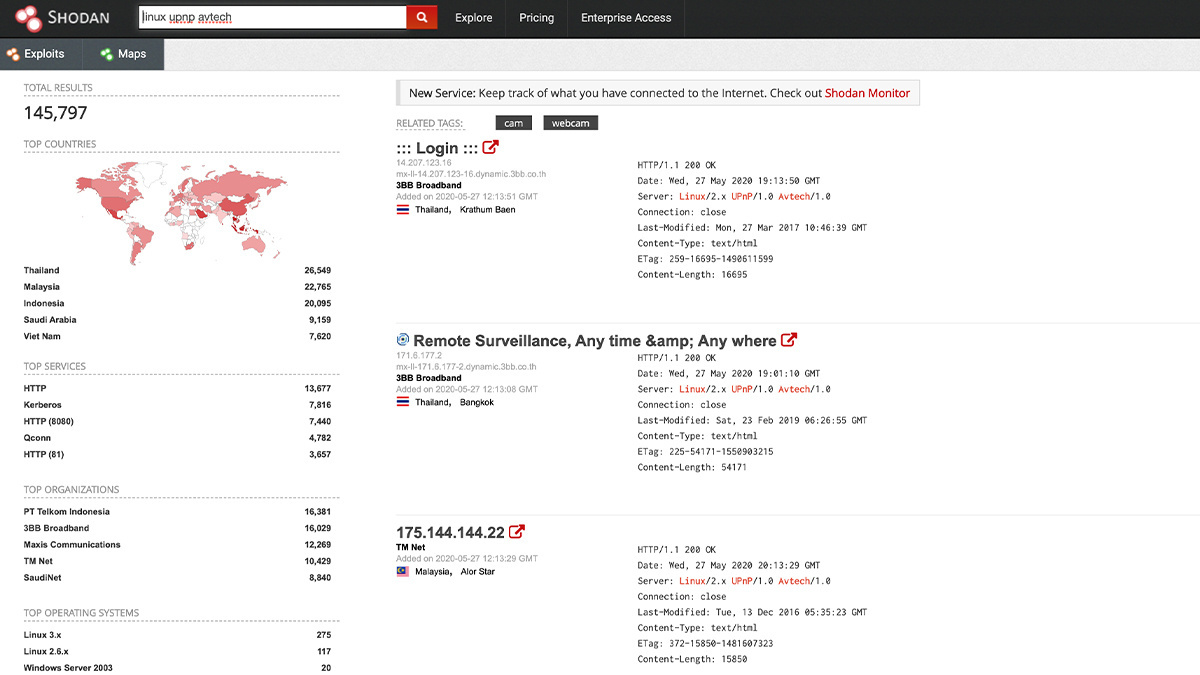
Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig
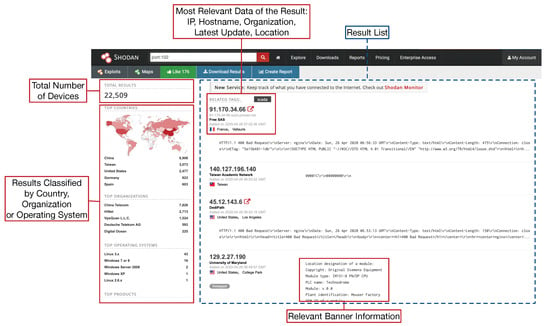
Applied Sciences | Free Full-Text | Use Case Based Blended Teaching of IIoT Cybersecurity in the Industry 4.0 Era
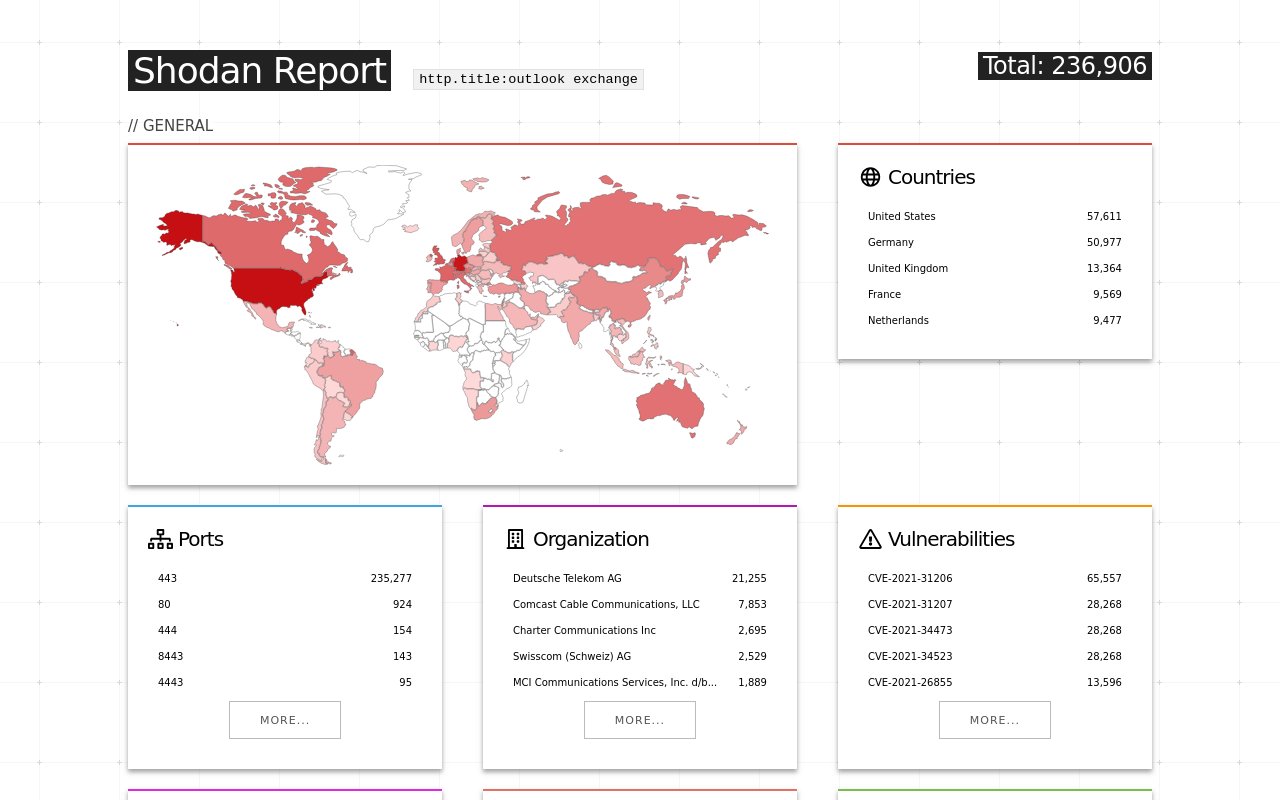
Shodan on Twitter: "More than 18% of Exchange servers remain unpatched for the ProxyShell vulnerability. Nearly 40% are vulnerable to CVE-2021-31206: https://t.co/7yetz9GoJw https://t.co/0r2AOQsibB" / Twitter

Shodan on Twitter: "Not sure what search filters are available? Check out our new filter reference page: https://t.co/kDlGDgpFms https://t.co/bUJX1D8ChQ" / Twitter





![Shodan, How to Avoid your Webcam and IoT devices from Being Hacked [Updated] - Shodan, How to Avoid your Webcam and IoT devices from Being Hacked [Updated] -](https://santandergto.com/wp-content/uploads/2019/06/shodan-explore-unsecured-webcams.jpg)