H-dropping areas based on SED data (left) and on the EDAC data (right) | Download Scientific Diagram
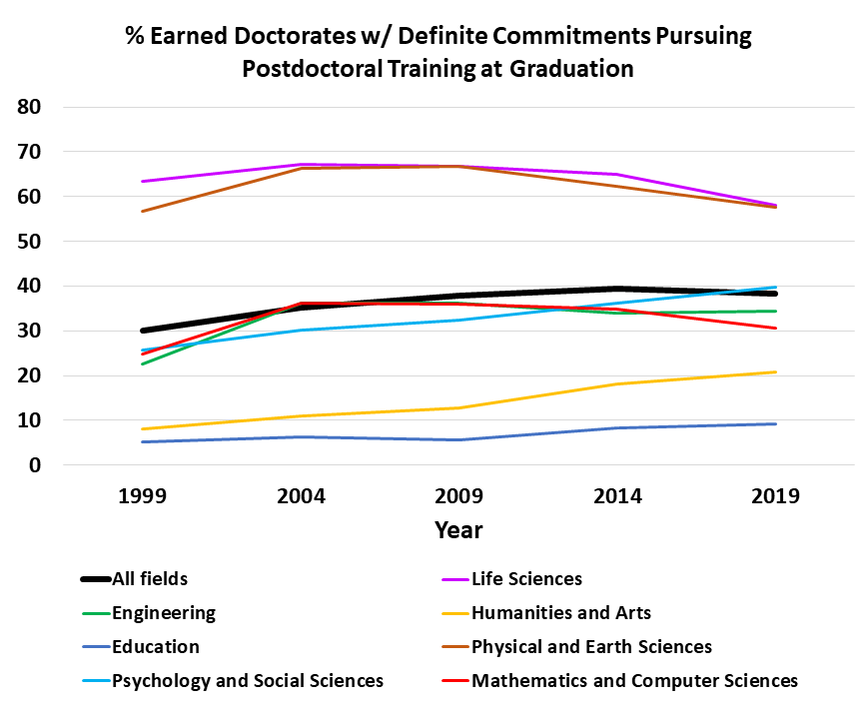
Ph.D. Recipients' Employment Trends: Insights From National Science Foundation Data - Christopher T Smith.com

The SED data and the accretion disk model for HE 0413-4031 shown as the... | Download Scientific Diagram

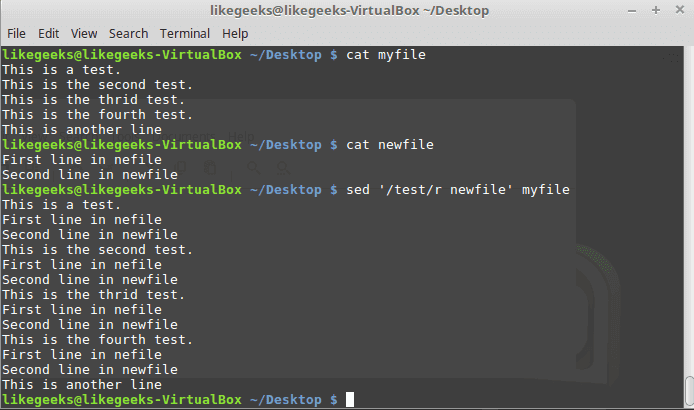
Regular Expression - How to Remove PII Data from File | How to Masked Personal Information from Json Logs | Regex Json Value and Remove #LinuxTopic - LinuxTopic
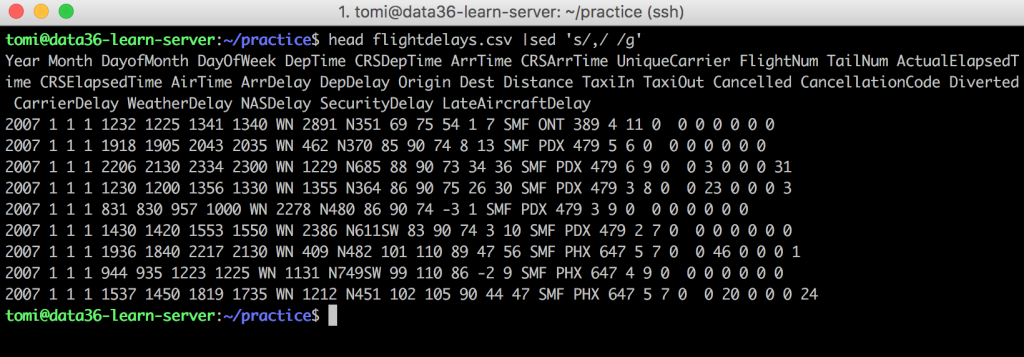
A brief introduction to Sed.. Pattern matching and text manipulation… | by Brendan Ferris | Analytics Vidhya | Medium