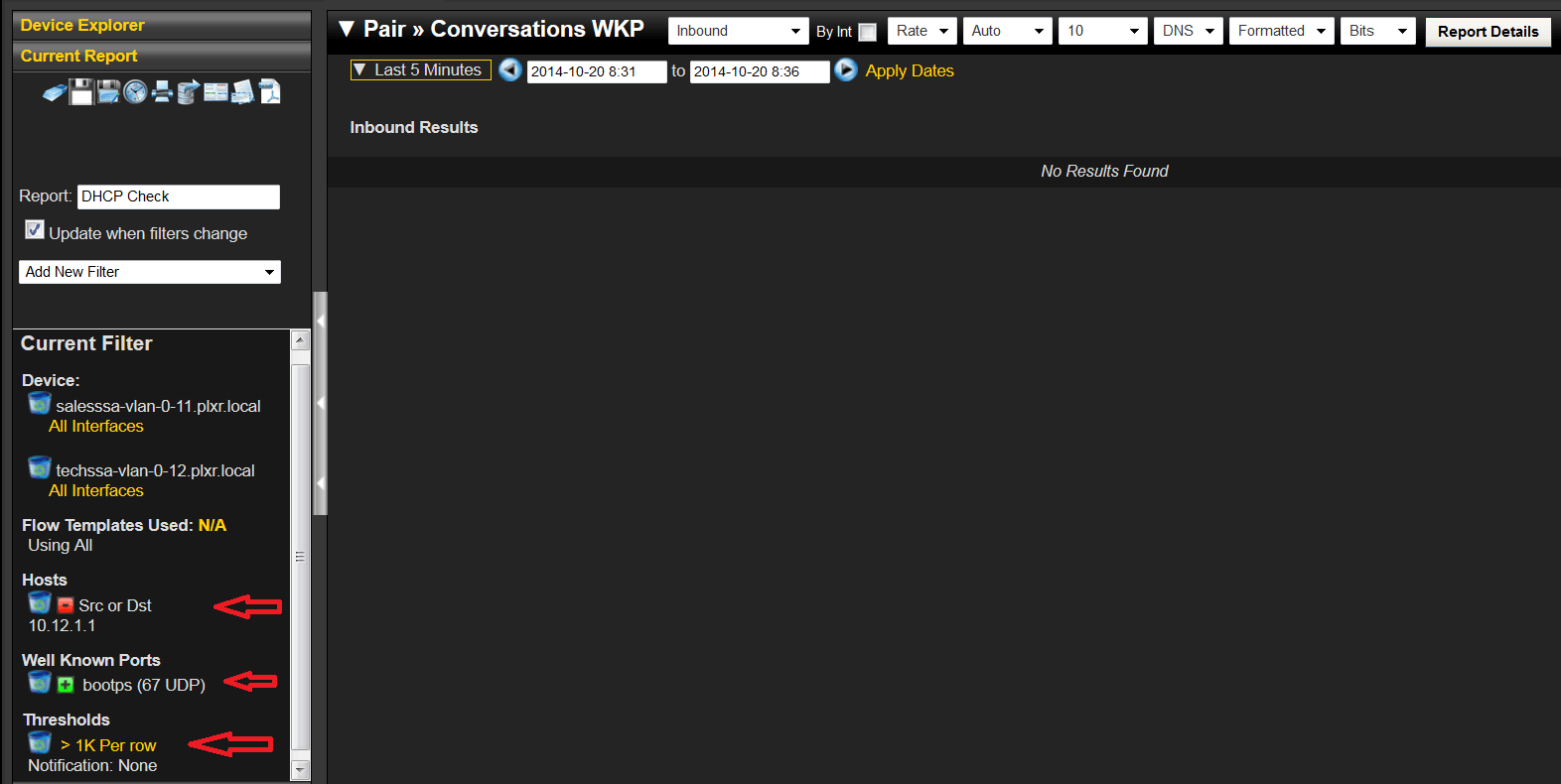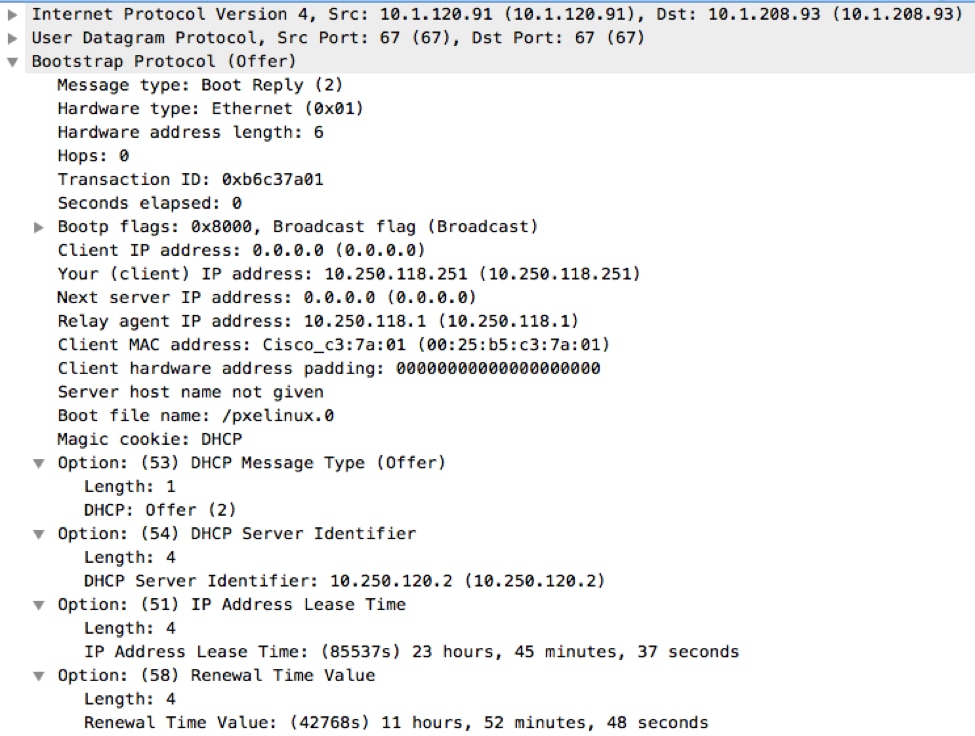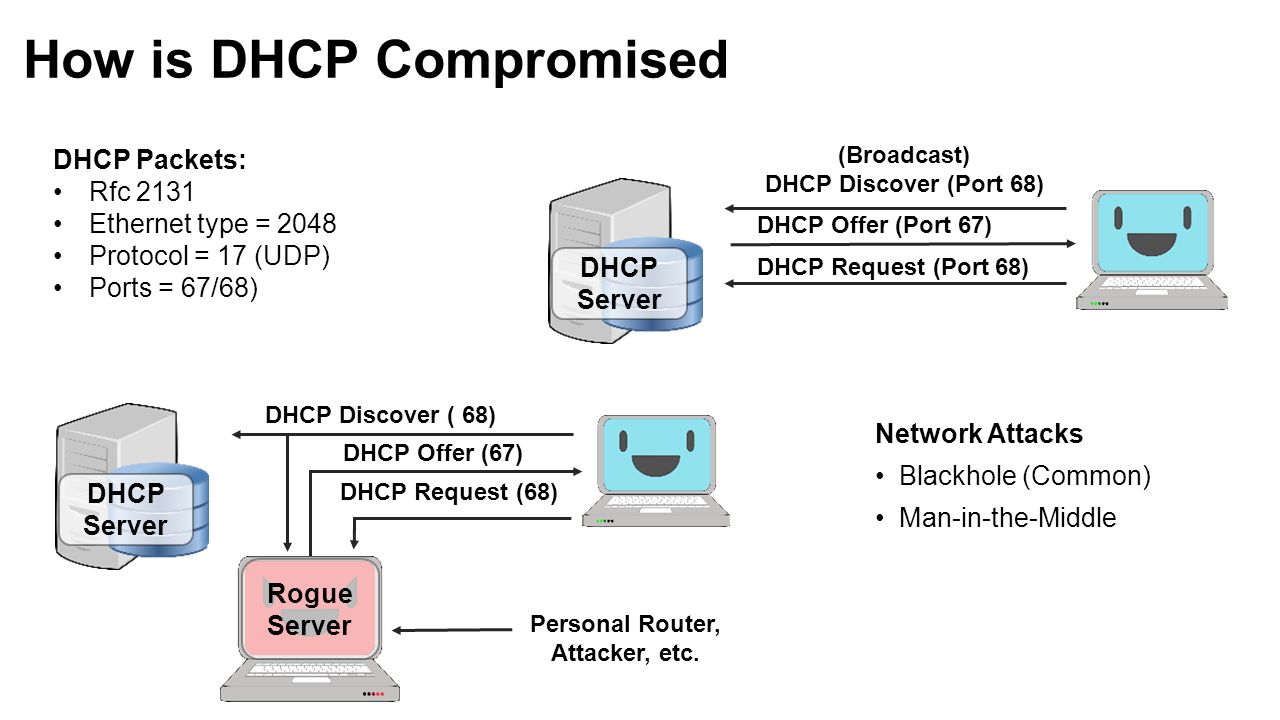
Leveraging SDN to Improve the Security of DHCP Presented By Jacob H. Cox Jr. For SDN NFV Security Workshop 2016 On 10 March ppt download

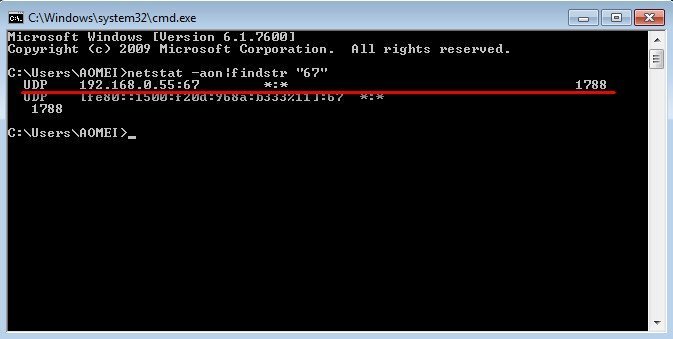
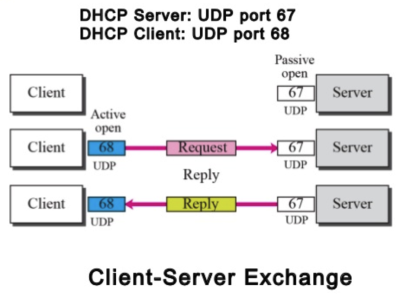
Why does DHCP uses UDP port 67 and 68 for the communication between the client and server? - YouTube
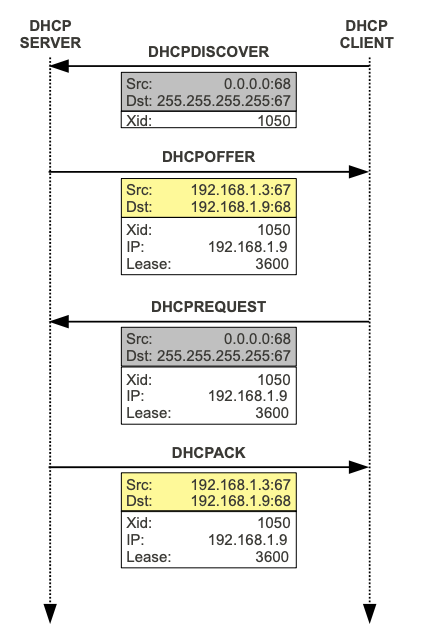
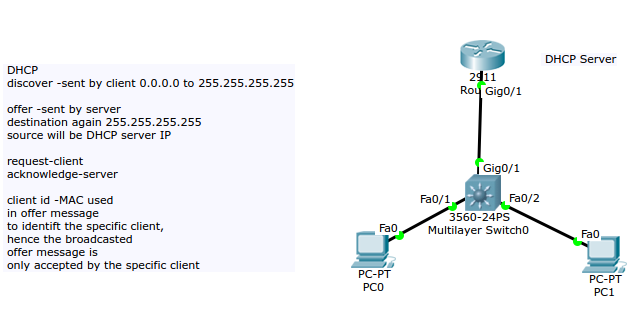
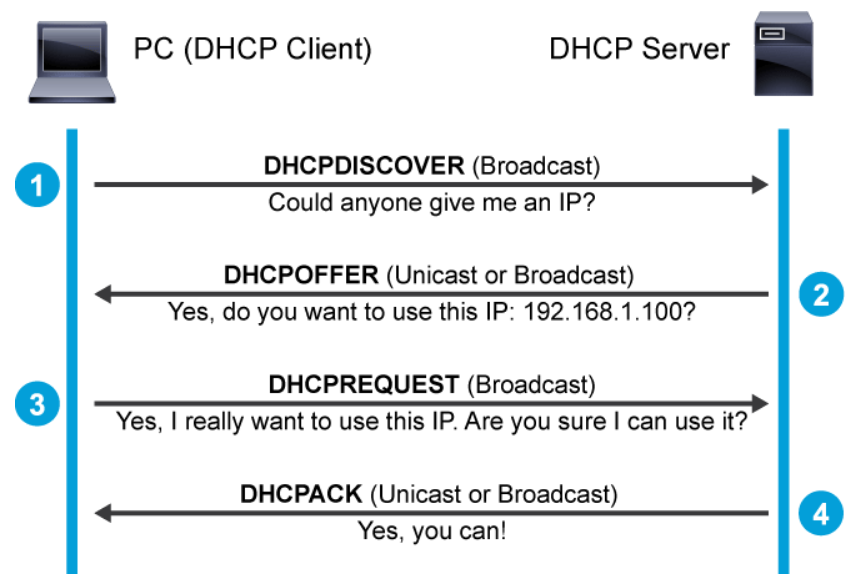
Internet Educational Series #5: DHCP (Dynamic Host Configuration Protocol) | by Markush | DataDrivenInvestor
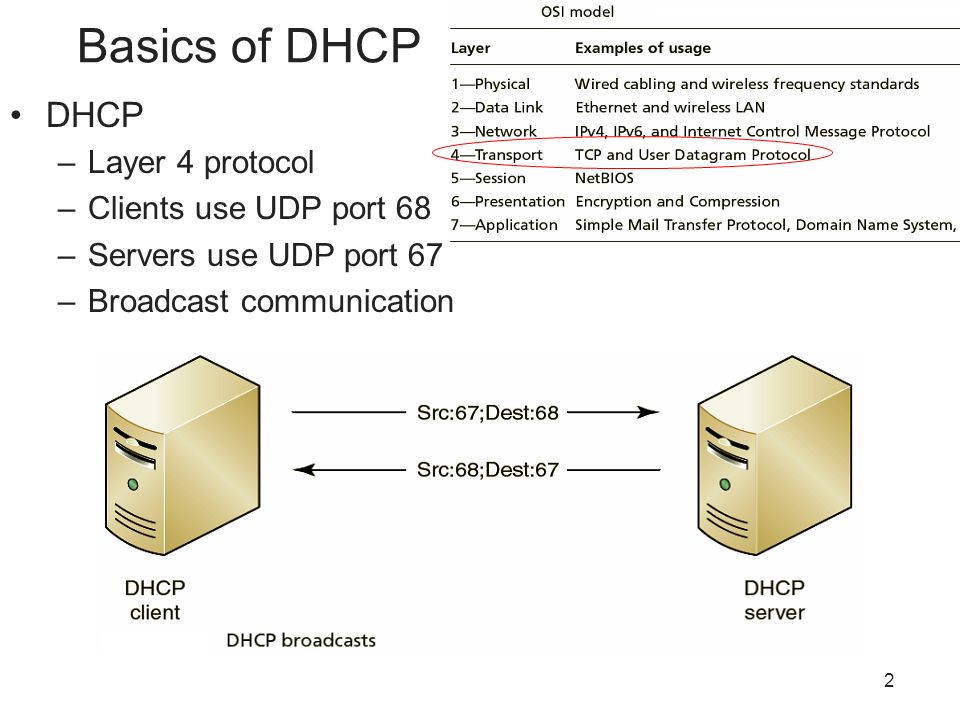
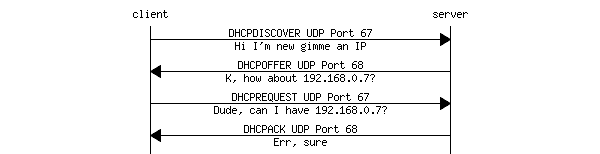
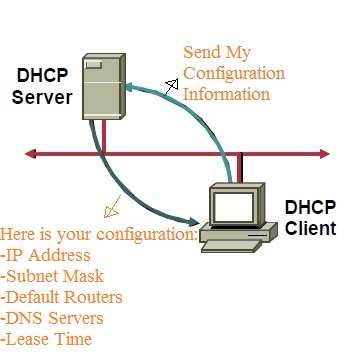
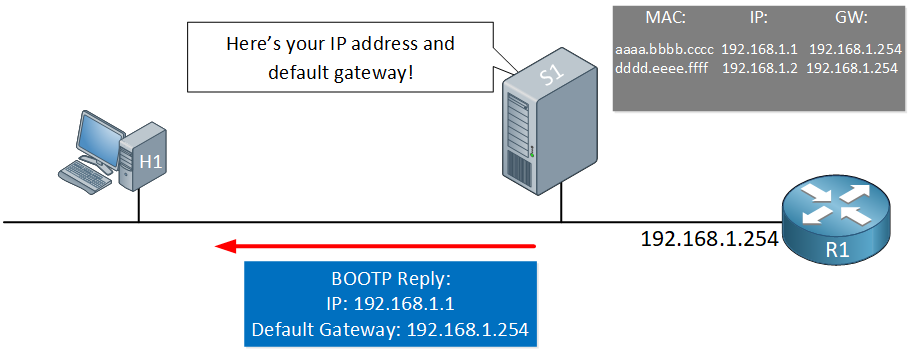




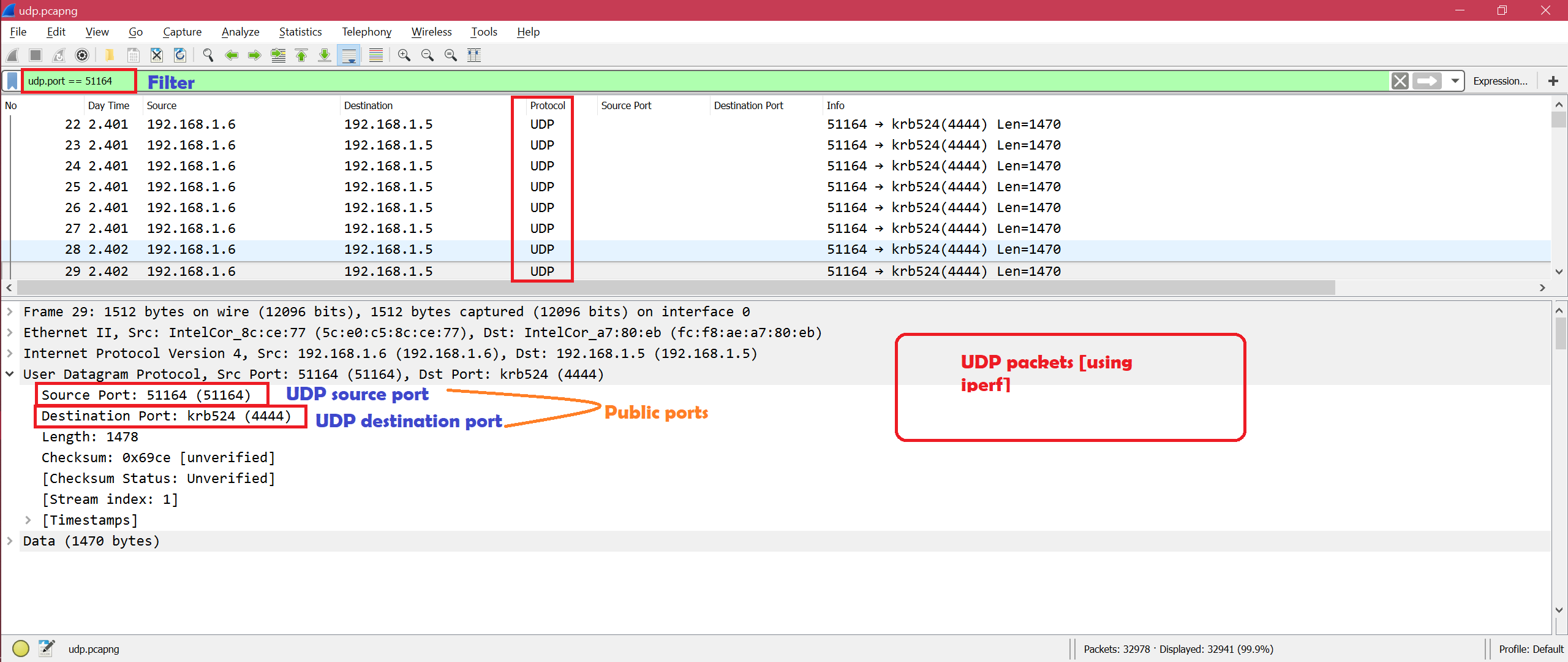
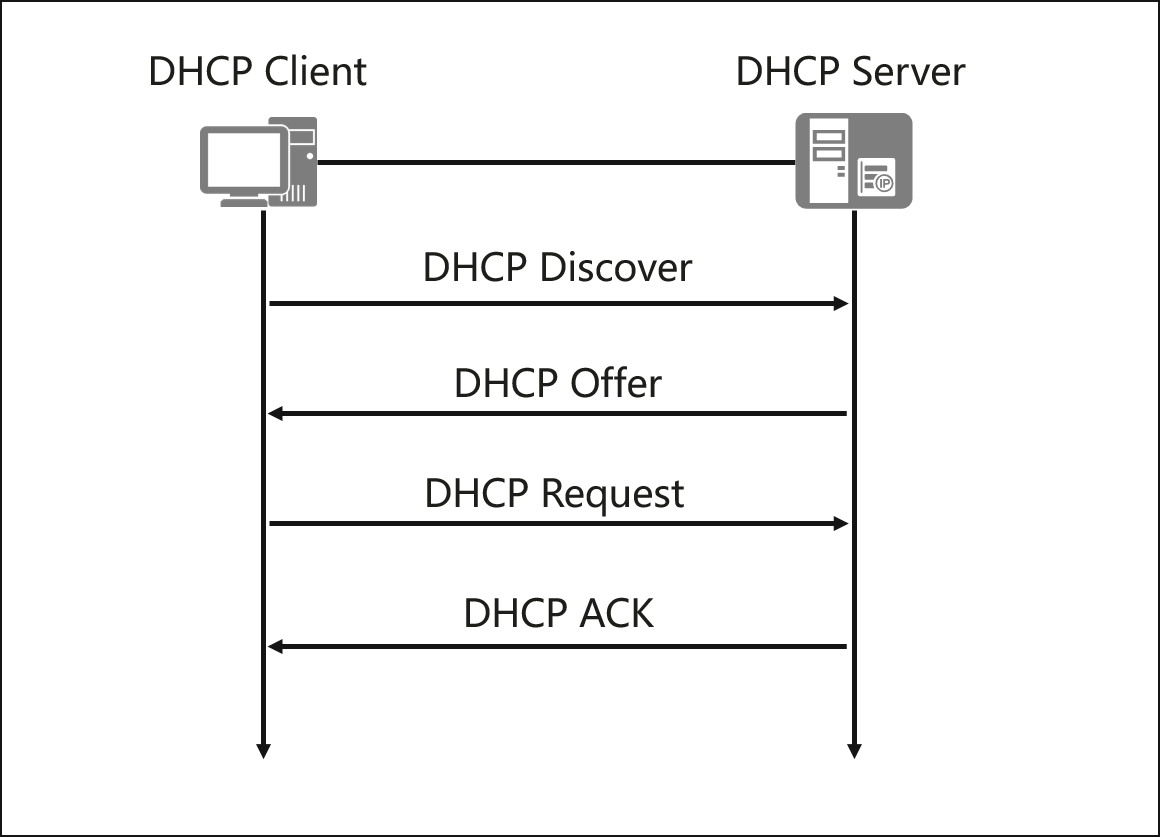
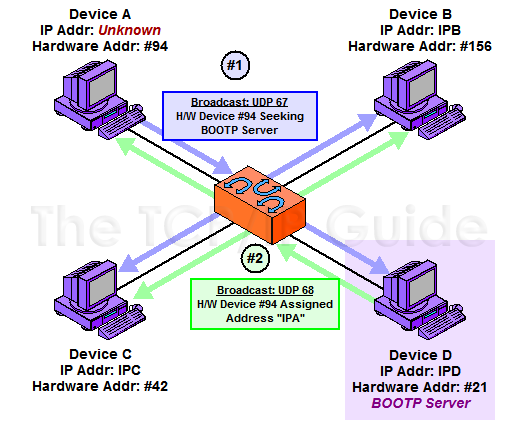
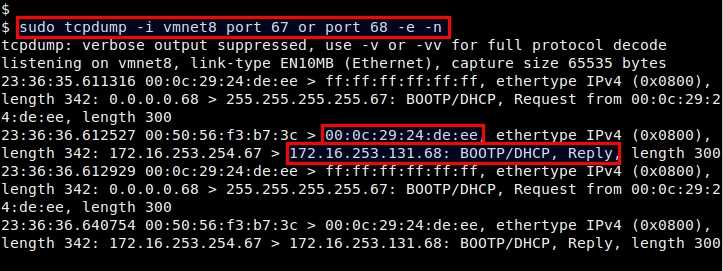
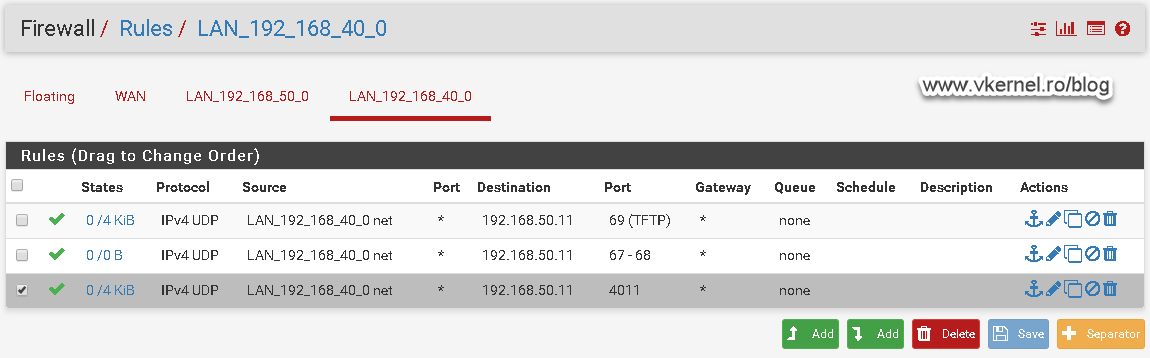
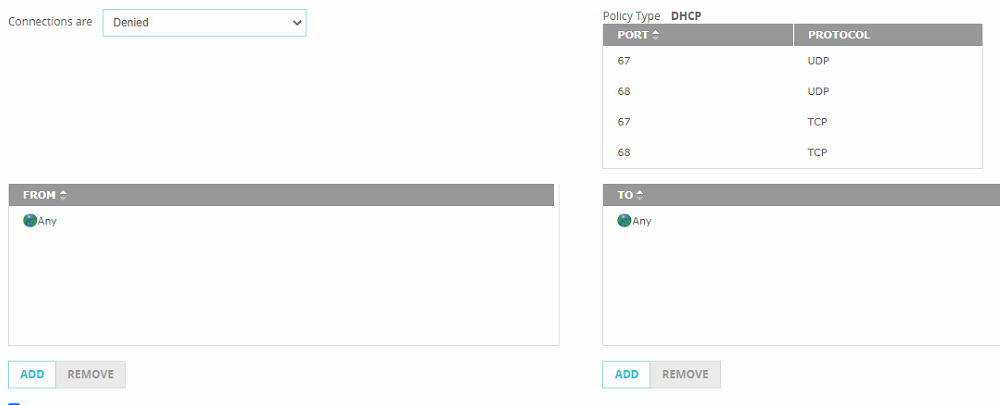
![Mikrotik.ID : [DHCP Security] - Pencegahan DHCP Rogue dengan Bridge Filter Mikrotik.ID : [DHCP Security] - Pencegahan DHCP Rogue dengan Bridge Filter](https://citraweb.com/images/artikel/DHCP_Rogue_Prevent/DHCP_proses2.png)