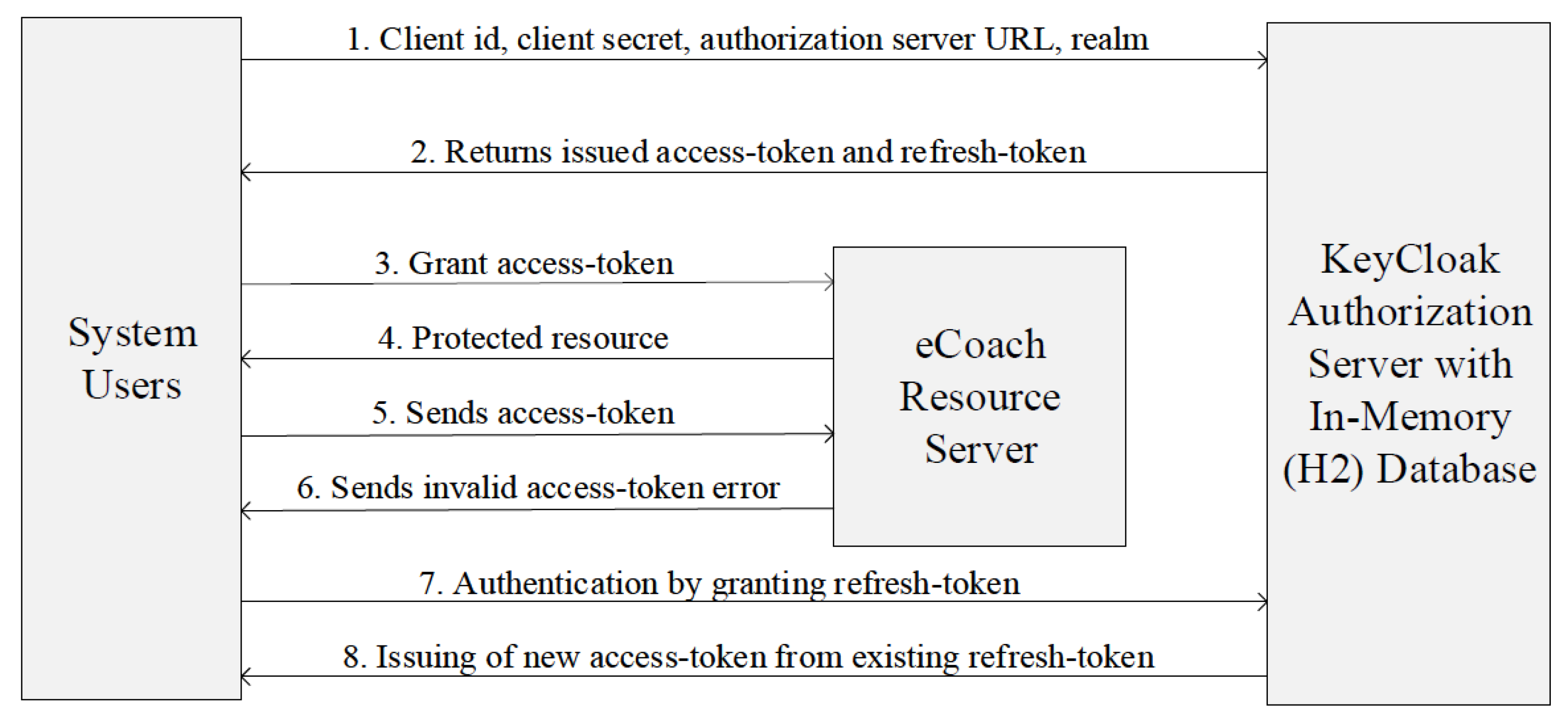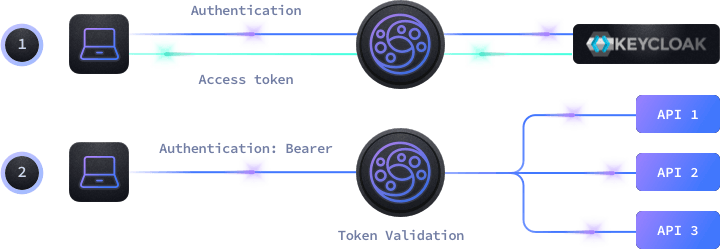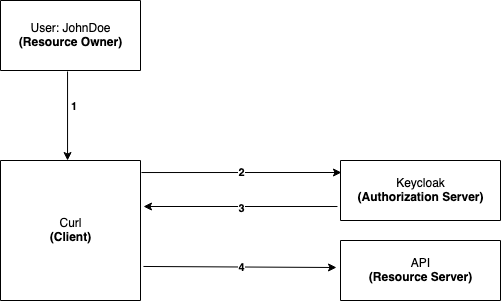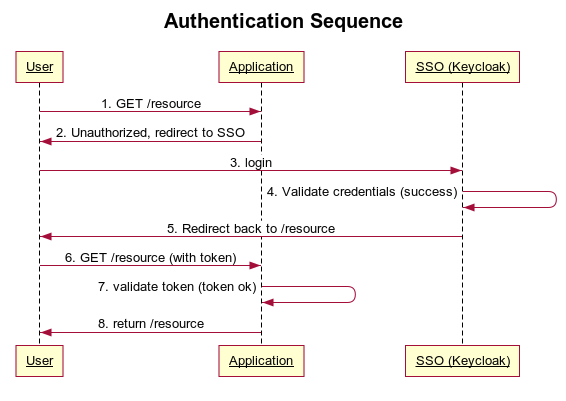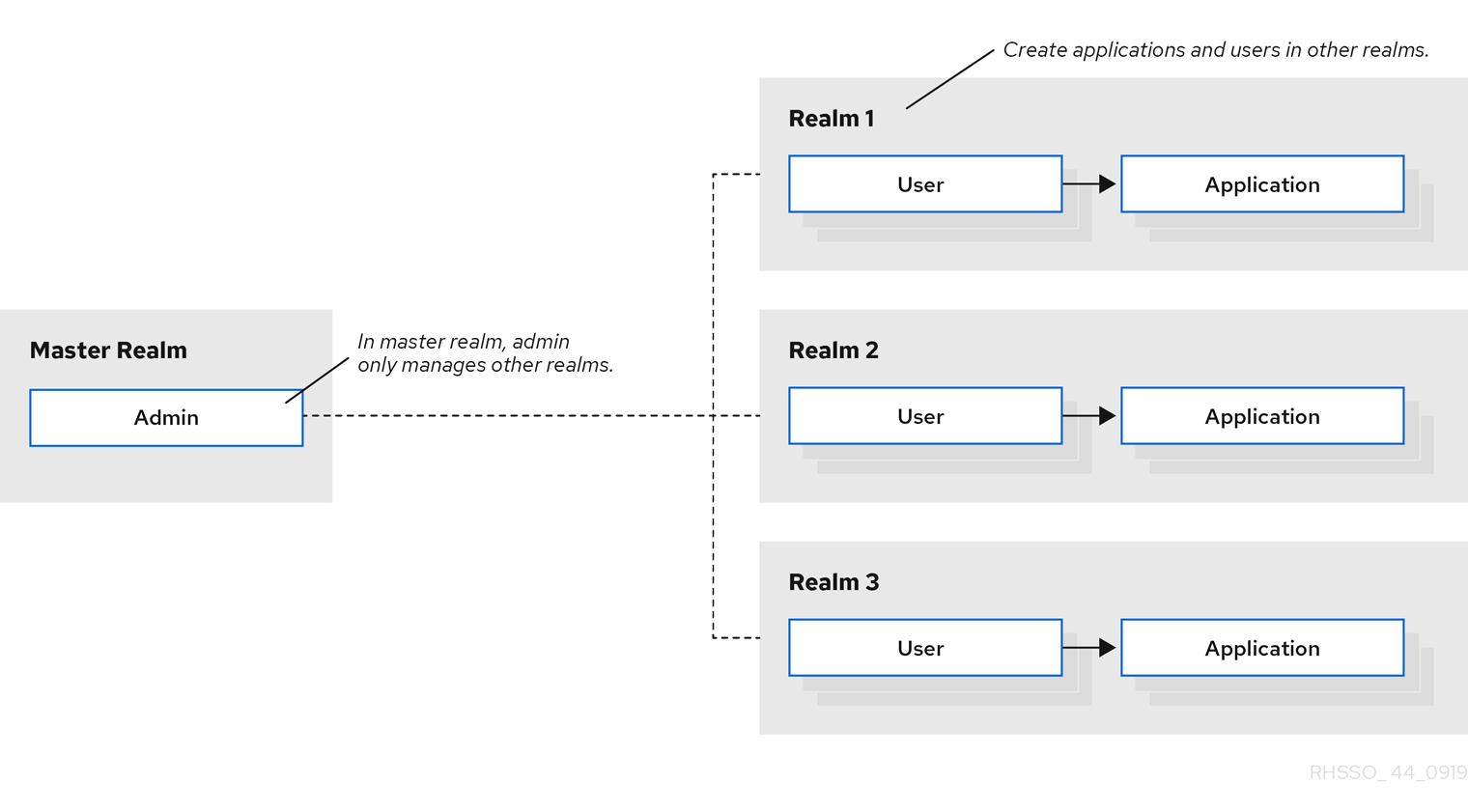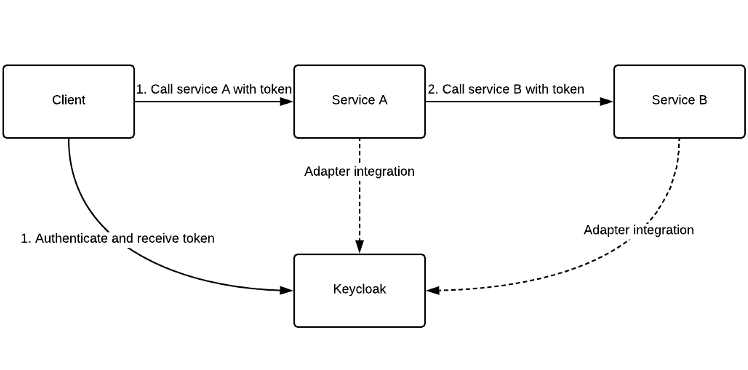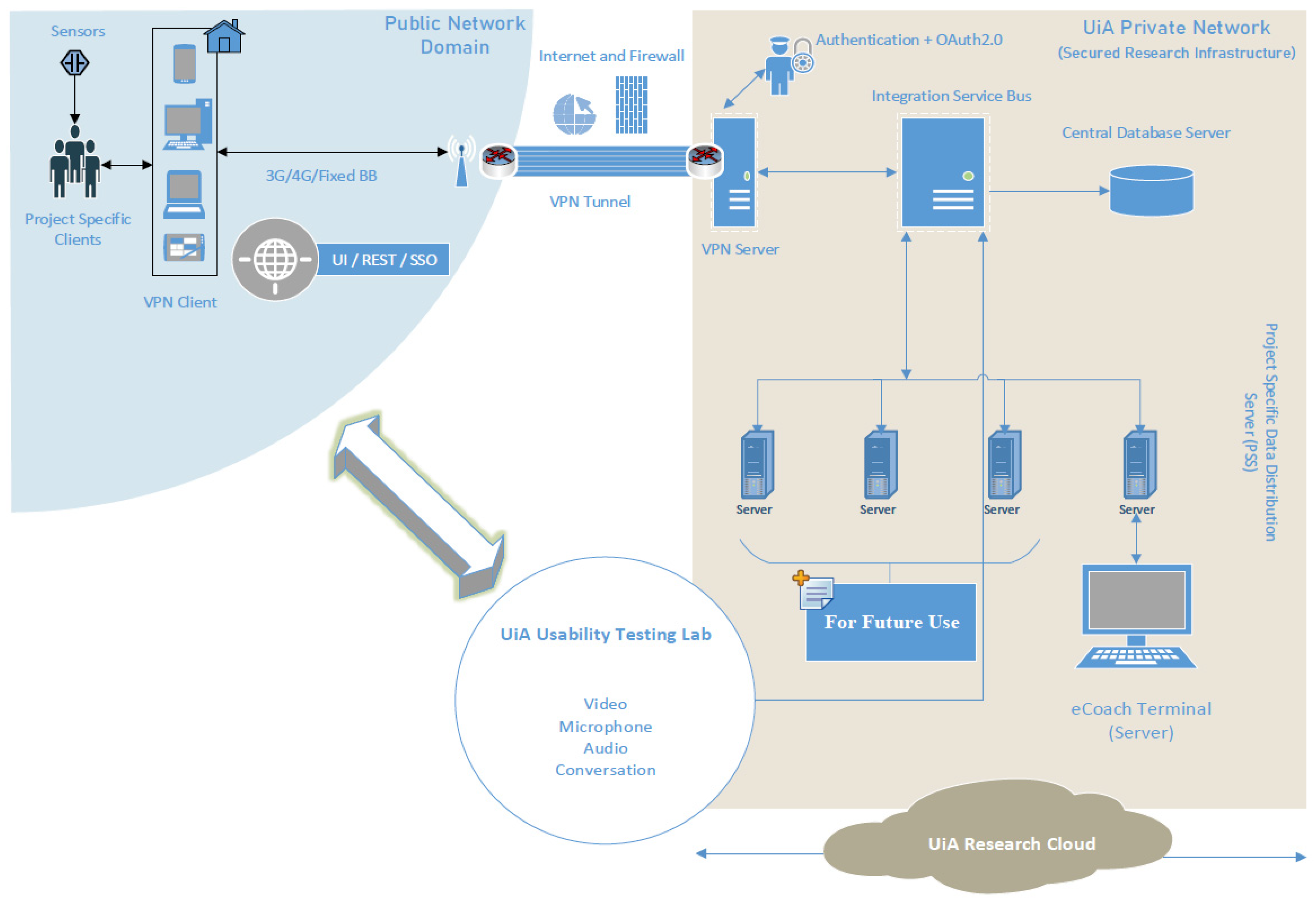
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study

java - How to Setup Keycloak + Spring Boot + Oauth2 within Microservice Architecture - Stack Overflow

Part 6 - How To Secure Distributed Apps with KEYCLOAK - Micro Service Rest API Bearer Only case - YouTube